When GCVE is provisioned, one of the initial configurations is to allow administrators to access the GCVE component management interfaces, including vCenter, NSX-T, HCX etc. This post is to summarize a few options to perform the connections.
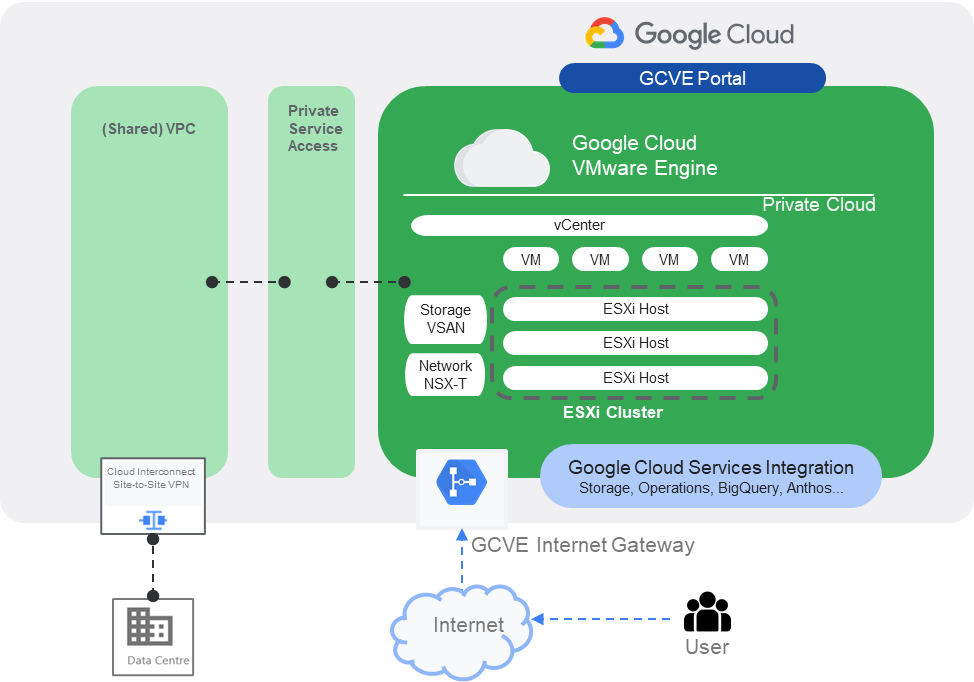
When GCVE private cloud is provisioned, the management interfaces of major GCVE components (vCenter, NSX-T and HCX) is provisioned automatically and can be identified in GCVE portal. To allow administrators to access these management interfaces, there are three options in general.

- Option 1: Site to Site GCP VPN or Cloud Interconnect
This option is to utilize the existing site-to-site VPN or Cloud Interconnect to allow administrators to access GCVE management interfaces from on-premise environment via the secured channel. This is the most recommended and secure way to access GCVE in hybrid environment. Via this option, you can treat this GCVE environment as an extension of your on-promise ESXi farm and access it via the same approach as the on-premise ones.

- Option 2: Point to Site GCVE VPN Gateway
This option provides a way to access the GCVE components in case the site-to-site VPN or Cloud Interconnect failed to connect. To continually manage the GCVE components, the point to site VPN could be provisioned to allow the user to connect GCVE directly via GCVE native point-to-site VPN Gateway.

To enable the point-to-site VPN Gateway, the below configuration is required:
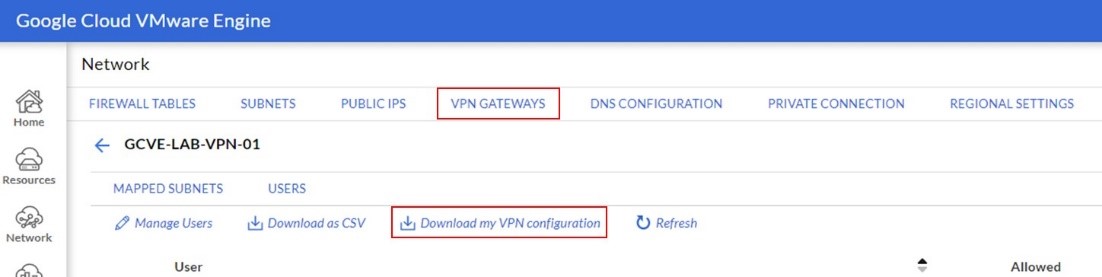
- In GCVE Portal, navigate to Network->VPN Gateway section.
- Create a new VPN Gateway. Provide the required information. Including location, client subnet (A new subnet used for VPN Client), mapped subnets (Define the subnets that the VPN user can access), users and etc.
- Once the VPN Gateway is created. Individual user can login to GCVE portal and “Download my VPN Configuration.”
- Then, the VPN user need to download the VPN Client from https://openvpn.net/community-downloads/ and import the VPN configuration file downloaded from previous step.
- Connect the VPN via “VMwareEngine-TCP-443” option.


- Option 3: GCVE Public IP Address Access
This is an alternative way to connect GCVE if point-to-site VPN can not function properly as stated in option2.
In this option, each GCVE Component management interface can be allocated with a public IP address. Administrators then can access the GCVE components via public IP addresses. In this option, the GCVE firewall is mandatory to be enabled to enhance the access security.
To enable the Public IP Access, the below configuration is required:
- In GCVE Portal, navigate to Network->Regional Settings, create a regional setting and enable Internet Access and Public IP Service.
- Navigate to Network->Public IP. Allocate public IP and attach to the GCVE component private IP as per the user preference. (For example, allocate a public IP and attach it to the private IP of vCenter management interface.)
- Navigate to Network->Firewall Tables. Create a Firewall Table and create FW rules to allow the access to the newly allocated public IP in previous step.
Summary
To access the GCVE, option 1 is no doubt the most recommended option since it constraint the management traffic in private network domain. The option2 and option 3 could be considered as a break glass solution in case the Site-to-site VPN or Cloud interconnect do not function properly.

